NetFlow Simulation Library: Advanced NBAR simulation
-
Table of Contents
-
Overview
After you install this patch, you'll be able simulate advanced NetFlow scenarios to generate dynamic traffic flows, including
-
Cisco NBAR
-
DoS Attack
-
Email Worm
-
W32gaobot SA Worm
-
W32Nachi Worm
-
W32NetSky Worm
-
Suspect data loss
-
ICMP Flood
- SYN Flood
The patch adds a new NETFLOW menu to the MIMICview menu bar to generate these different NetFlow traffic patterns.
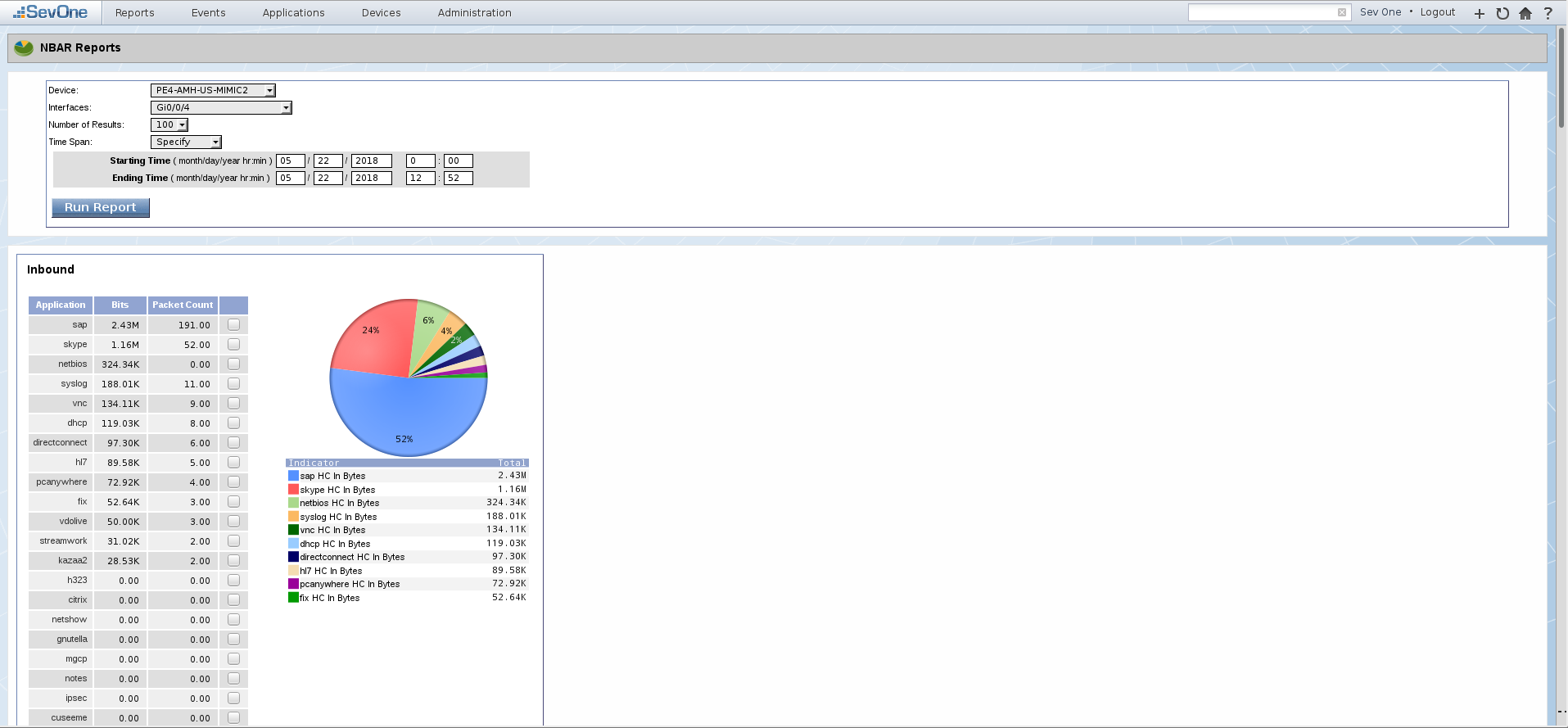
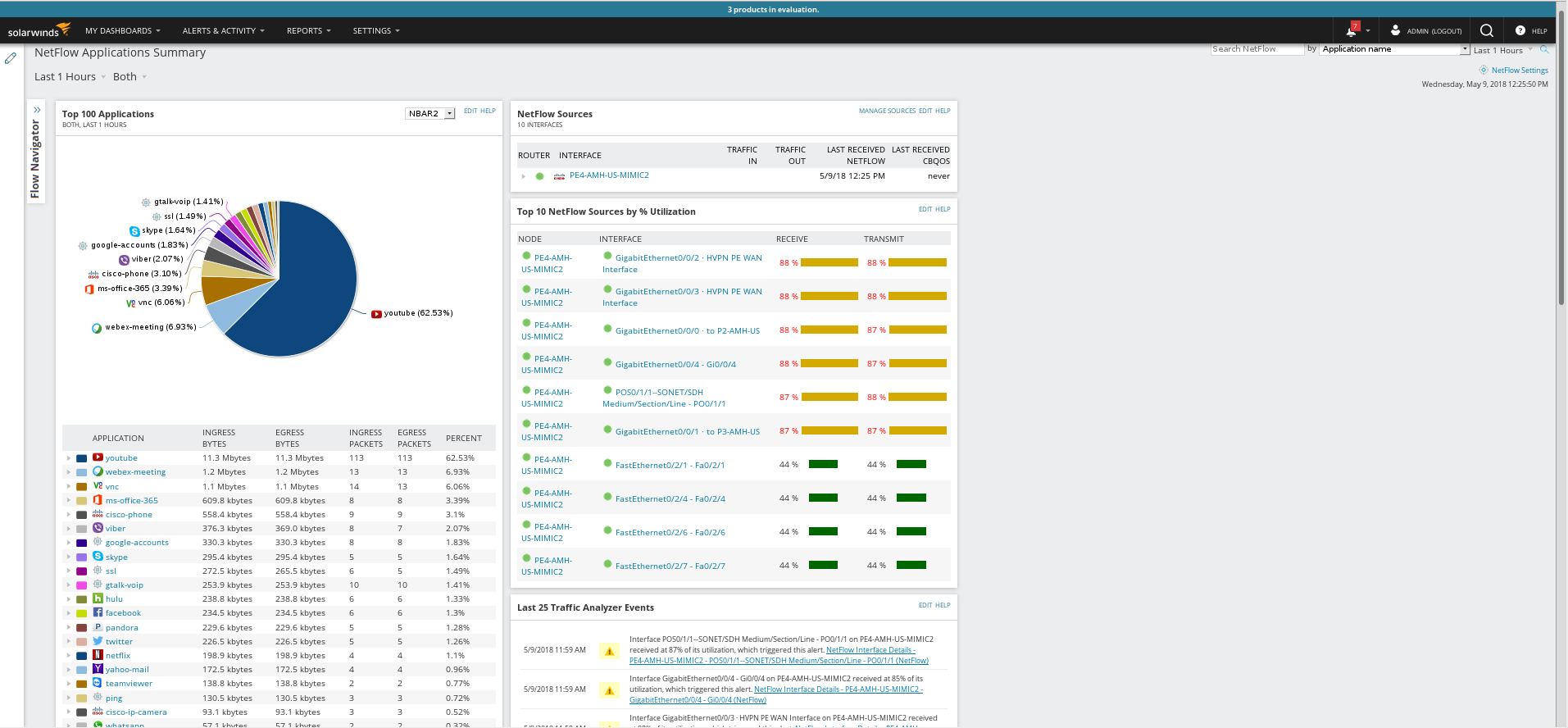
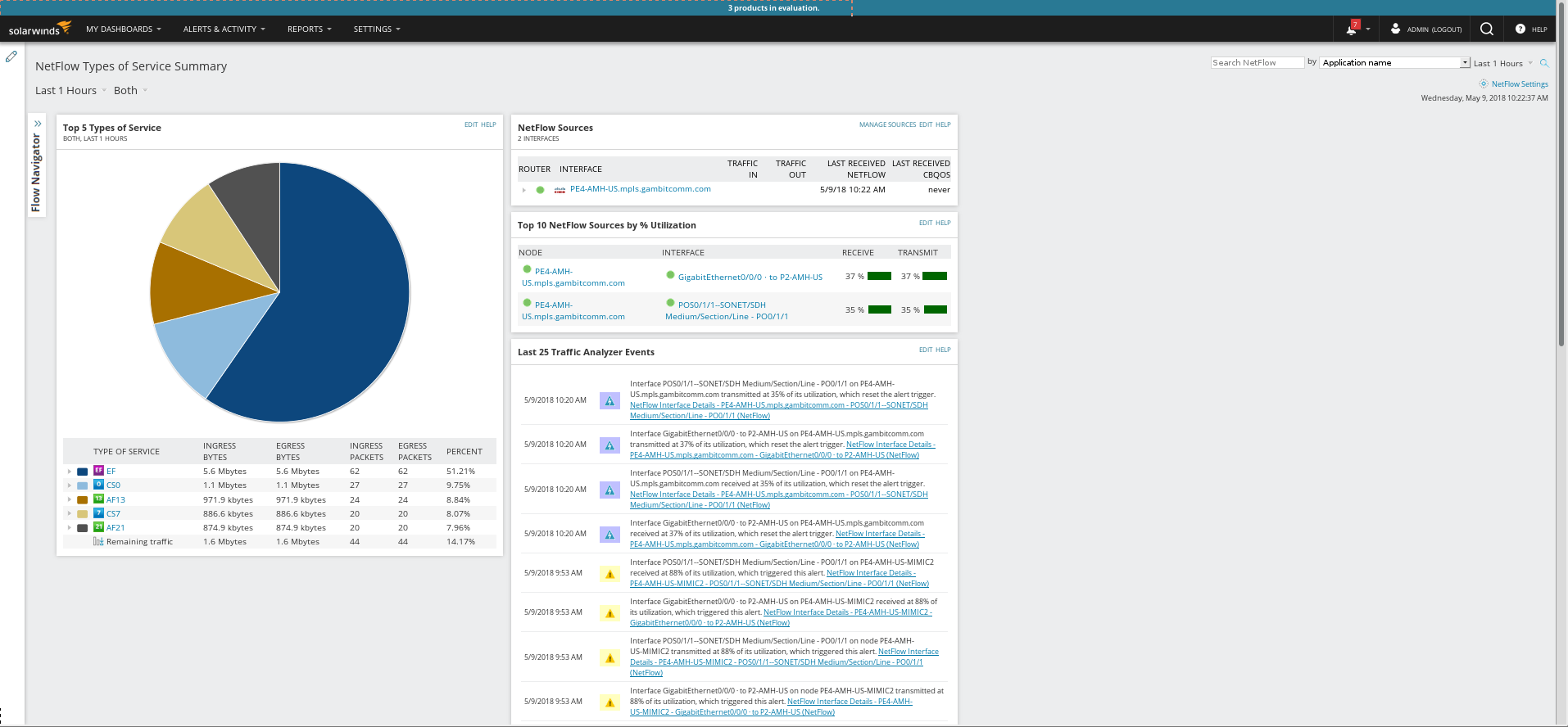
This is Plixer Scrutinizer visualizing generated NBAR traffic patterns:
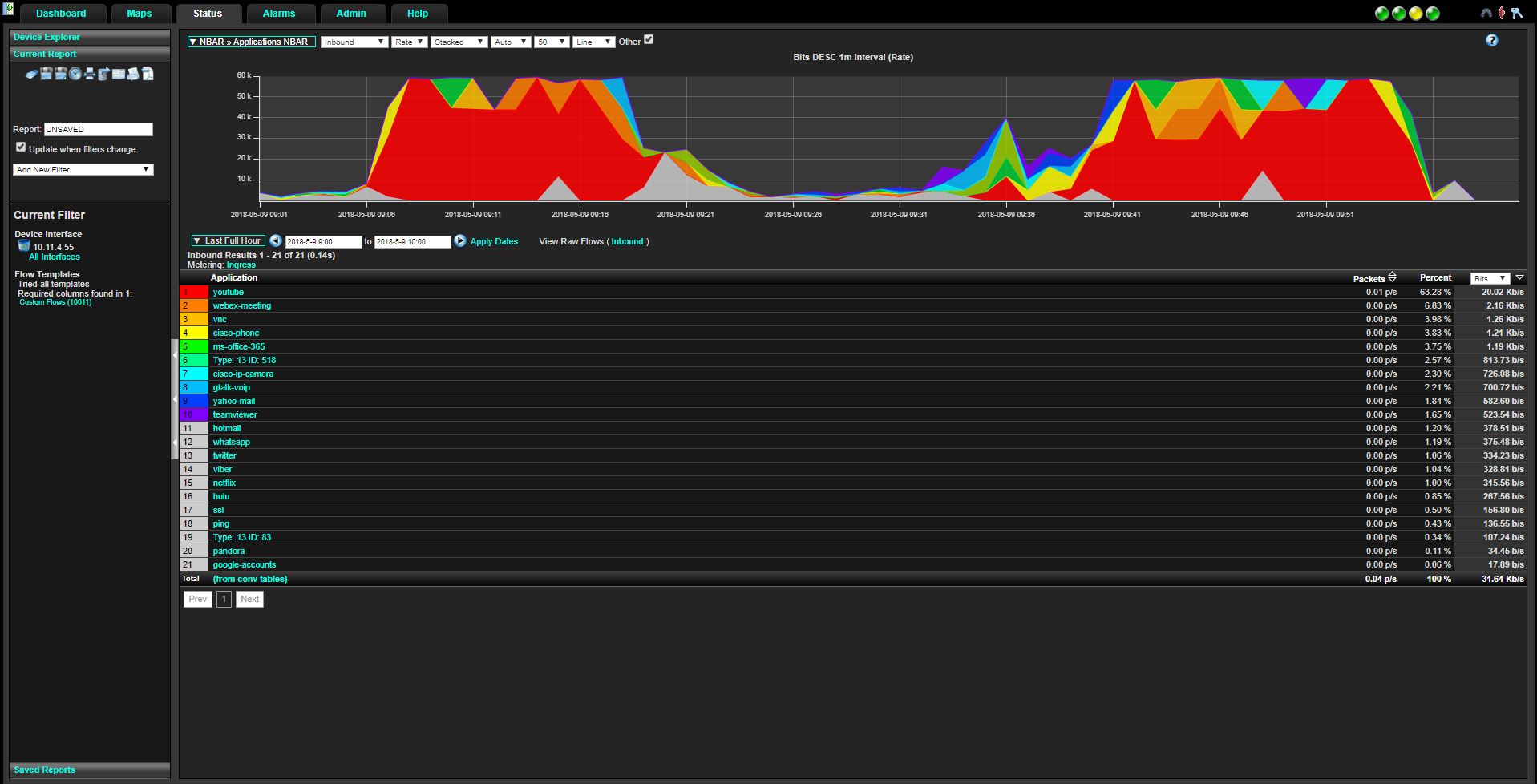
and SevOne
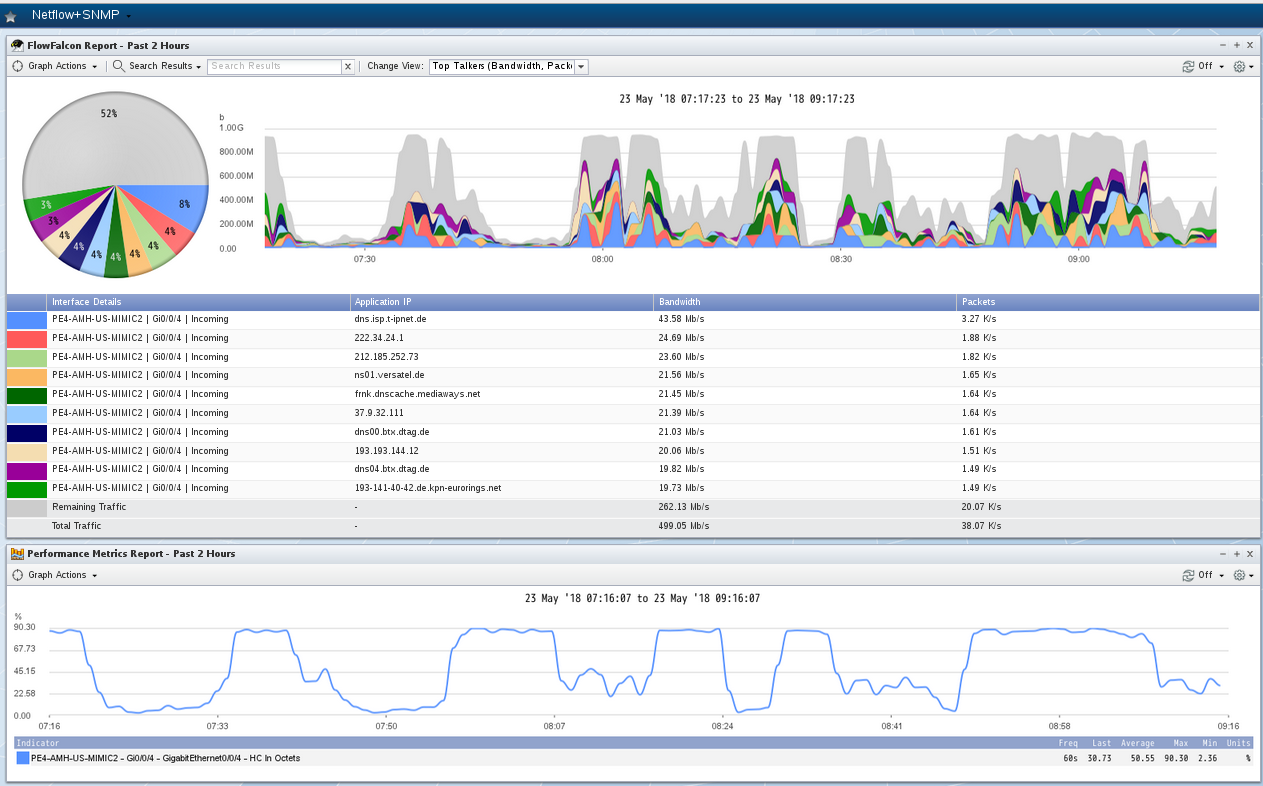
and Solarwinds
-
Cisco NBAR
-
Prerequisites
To run this simulation, you must have installed the optional NETFLOW module as documented in the NETFLOW Protocol Module Guide of the online documentation.
Once this package is installed, restart MIMICview with File -> Exit and a new NETFLOW menu will appear in the top menu bar.
-
Usage
Each of the menu items in the NETFLOW menu configures the desired range of agents with
-
NetFlow configuration file
-
collector
- port
to generate the desired traffic pattern.
After setting the desired traffic pattern with the menu item under the NETFLOW menu, you can customize the values for the traffic levels
General steps to configure agents to run the Netflow action scripts
-
Configure traffic pattern with NETFLOW menu item.
-
set agent store variable to define desired interfaces for the flows
- Select desired agent
- invoke Edit->Variable Store or Agent->Variable Store menu
- select Agent branch
- click Add
- Enter as in example below to match exact script path
Variable: INPUT_SNMP Value: 3 5 7 Variable: OUTPUT_SNMP Value: 1 2 5
or in a MIMICShell or script as:
mimic agent store set INPUT_SNMP "3 5 7" 1 mimic agent store set OUTPUT_SNMP "1 2 5" 1
Other agent store variables that can be changed run time to provide values as list or range:
IPV4_SRC_ADDR_RANGE (e.g., 10.11.10.1,10) IPV4_SRC_ADDR (e.g., 10.11.10.1 10.11.10.5 10.11.10.7) IPV4_DST_ADDR_RANGE IPV4_DST_ADDR APPLICATION_TAG L4_DST_PORT SRC_TOS IN_BYTES IN_PKTS ifrate(all) (e.g., to change interface utilization on all indices) ifrate(1) (e.g., to change interface utilization on specific index)
- start agent(s) and each will start generating flows
Steps to simulate increased interface utilization in SNMP ifTable, cbQosCMStatsTable and NBAR2 Netflow
This will simulate:
-
Increased utilization on one of the router interfaces shown via SNMP
-
Increased utilization on the same interface shown via NetFlow (NBAR2)
- CBQoS queue showing that the priority queue is dropping traffic because of the increase of the offending traffic type
-
Invoke NETFLOW -> Configure CBQoS NBAR... menu item
Device: use simulated device that has cisco/CISCO-CLASS-BASED-QOS-MIB. For example, cisco-12410.random from MIMIC Cisco Device Library has that MIB. You can download the device library using Wizard -> Update in MIMICview.
-
Invoke NETFLOW -> NBAR High Youtube Usage menu item to change
high rate of NBAR2 flows for Youtube application as well as high
utilization in ifTable and cbQosCMStatsTable.
- Invoke NETFLOW -> NBAR Normal Usage menu item to change back to normal usage rate of NBAR2 flows for all applications as well as normal utilization in ifTable and cbQosCMStatsTable.
-
NetFlow configuration file
-
Compatibility
Download the "Netflow Compatibility" update to view compatibility against third party applications.
